Platform
Downtime: The Real Cost Of Ransomware
Ransoms are just one portion of the total cost of a ransomware attack. Recovery becomes costly as businesses suffer the majority of their losses through lost productivity, and backups don’t preclude expensive recovery.
Alberto Sigismondi
Feb 27, 2024
Share
Modern-day ransomware attacks are vastly different from the malware attacks from the past. Threat actors have become so sophisticated in their techniques that it’s become tougher and tougher for companies to detect and recover from these malicious activities.
Since 2016, more than 4,000 ransomware attacks have happened daily. And a host of new and evolving cybersecurity threats are continuing to put companies on high alert.
Just this year, a cyberattack forced the shutdown of Colonial Pipeline—one of the largest fuel pipelines in the United States—and led to widespread shortages at gas stations along the east coast. In order to quickly get systems up and running, Joseph Blount, the CEO of Colonial Pipeline, authorized the ransom payment of nearly $4.5 million to the hacker group. “It was one of the toughest decisions I have had to make in my life,” Blount said in a CNBC interview.
Resisting ransom payments is difficult. But paying the ransom contributes to the false promise that it will be quicker and easier to undo the damage—when in reality, it's about prioritizing the restoration of critical data, applications, and systems needed to run the business.
Why Paying Up Doesn’t Always Pay Off
Many organizations feel tremendous pressure to pay ransoms because they can’t afford to be offline or locked out of mission-critical systems and applications for days or weeks. The average downtime a company experiences after a ransomware attack is 21 days.
Downtime is the most costly aspect of a ransomware attack. Recovering from a ransomware attack is 10 times the size of the ransom payment, according to Sophos research.
The study also found the average total cost of recovery from a ransomware attack has more than doubled in a year, increasing from $761,106 to $1.85 million in 2021. It’s no surprise that this figure can potentially be much larger for organizations in certain industries, such as financial services, energy, and healthcare, where there’s a more direct impact on consumers.
Backups Only Address a Small Part of Ransomware Recovery
For more than 50 years, backup software has proven reliable to restore data after application failures or data corruption issues. However, modern businesses today rely on enterprise apps, and data is mission-critical.
For any large enterprise with modern applications, they might have thousands, or hundreds of thousands, of transactions that occur in a single day. They can’t afford to protect data with a once-a-day backup. And many backup softwares have legacy security models, which make them vulnerable to compromise and for cyber attackers to demand and control snapshot data.
Second, restoring from backups at scale requires a significant amount of effort. The process of restoring from backups has to be perfectly coordinated across a number of groups working together, notably backup and storage administrators, application DBAs, developers, and networking personnel.
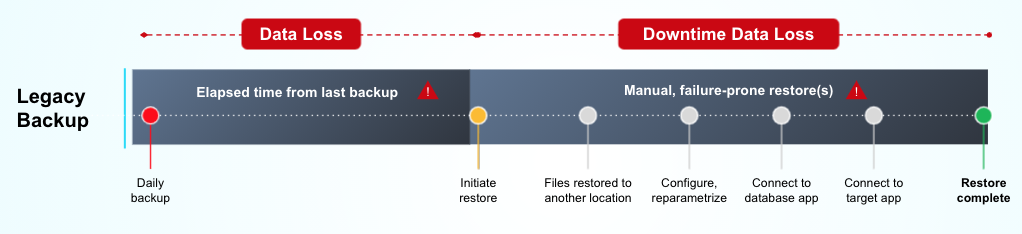
And even if it’s a successful backup, companies can only recover a file or a VM. Teams still need a way to stand up and configure the application and database servers to get an application fully up and running.
Third, ransomware attacks involve huge undetected dwell times. A recent IBM study found the average time to detect and contain a data breach is 287 days (212 to detect, 75 to contain). The timestamp delta between the last known good backup and the production application state right before the attack can be large. This gap typically represents significant losses in data, which adds to total impact.
Lastly, backup solutions have no data theft protection. There is data sitting at risk in development and test environments, and there’s no way backup solutions can secure data once a cyber attackers have made their way into the environment.
Well stated by risk and security expert Paul Proctor in a recent blog post:
“You know when the first time most organizations test restore? After they’ve been hit by ransomware. And that is the single biggest factor in whether it devastates the organization or takes a couple of hours to clean up.”
“If you strengthen your backup and test restores on all your critical business processes, the cost of recovery will always be less than paying the ransom for an uncertain outcome.”
Modern Companies Need a Modern Solution That Enables Automated Recovery
Delphix offers a modern, fully automated application recovery solution that allows organizations to instantly deploy a zero trust ransomware recovery environment to minimize downtimes after an attack.

First, it provides close to real-time data synchronization with production systems, in many cases without the need to be connected with production. The data is stored in a proprietary write-once, read-many immutable snapshot-based architecture (called Delphix Data Vault), which provides stringent security features to prevent any data changes or deletions, not even by administrators.
Second, it adds a multilevel detection mechanism that is fully customizable to the specific application environment. It recognizes encryption of blocks, files, data in files, and changes in stored procedures.
Finally, it provides a zero trust model with fully automated instant recovery capabilities that can be integrated via APIs with IT services and alerting tools—such as ServiceNow, AppDynamics, Datadog—as well as orchestration tools like Jenkins to instantly provision reliable production data to any environment in minutes, no matter the dataset size and with no manual intervention required. It’s 100% automated.
Because the data is provisioned in virtual datasets and served from the Delphix storage architecture, it can be rewound to any point in time. Once the virtual dataset is used to recover applications, it can easily be destroyed without affecting the original stored backup data, which remains immutable.
Furthermore, Delphix provides continuous compliance with data masking. We've seen a number of large high-profile companies, like Uber, where malware finds its way in through lower environments first. The reason for this is that investments in security for dev/test environments are historically lower than for production systems. By leveraging data masking, the result is that all non-production applications are running with high-quality data that values nothing in the hands of malicious actors, dropping the overall risks for extortionware and lockerware to zero.
Final Thoughts
Ransomware attacks have become so common that it's no longer a matter of if but when, and the aftershocks are instant and painful. The pricey ransomware payouts, downtime costs from shutting down company operations, and permanent loss of company data can be detrimental to companies.
An organization's readiness level in each stage of the incident response process will determine whether one pays the ransom versus not. In other words, the less prepared you are, the easier it will be to pay the ransom.
Having a sound prevention and recovery plan for ransomware must be a top priority for every organization, and it should not stop at solely implementing traditional cybersecurity and backup applications. These two applications serve their purpose, but they can’t be relied on as the only solution.
Preventing long downtimes requires activating a recovery plan for your business-critical applications. A modern approach that leverages a fully automated, zero-trust recovery model is a must-have, and organizations can leverage tools like Delphix that are capable of automating the process in full—from detection to recovery.
Learn more about how Delphix closes a critical gap in ransomware protection and provides continuous data protection.